Error: is not authorized to perform dynamodb:* on resource

Answered by Rafal Wilinski
What's Causing This Error
This error occurs when the IAM Role associated with the service performing a DynamoDB operation does not have the required permissions.
For example, this error would get thrown if a Lambda function does not have permission to perform a query operation and executes a query.
Solution - Here's How To Resolve It
To resolve the error, you will have to bind the required policy to the IAM Role of the service.
First, visit the IAM Console and search for the role that needs the DynamoDB policies. For example, the role that is bounded to the Lambda function.
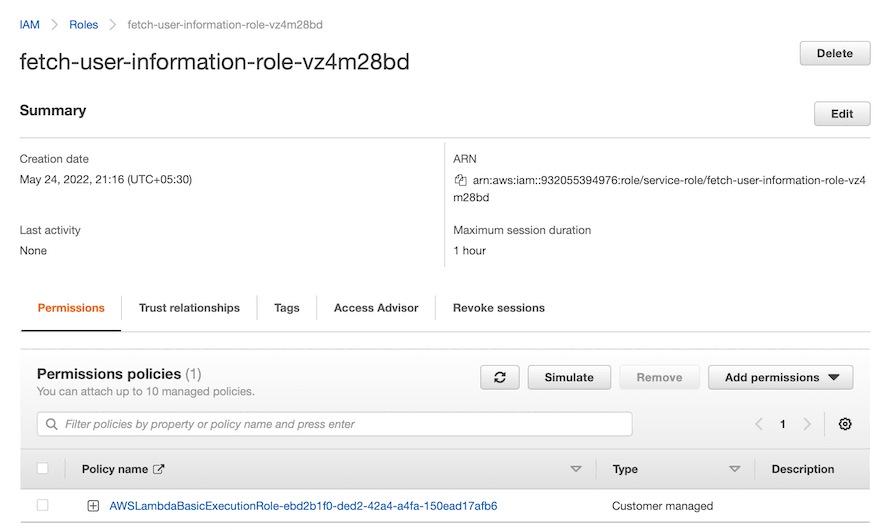
Figure - Viewing the Role bounded to the Lambda function
Afterward, click on "Add Permissions" and select either "Attach Policies" or "Create Inline Policies."
Selecting "Attach Policies"
If you select "Attach Policies," you can choose the DynamoDB policies managed by AWS. Please note that some of these policies provide full access to DynamoDB, giving a Lambda function to perform costly operations such as a "Scan."
The figure shown below highlights the policies for DynamoDB that AWS manages.
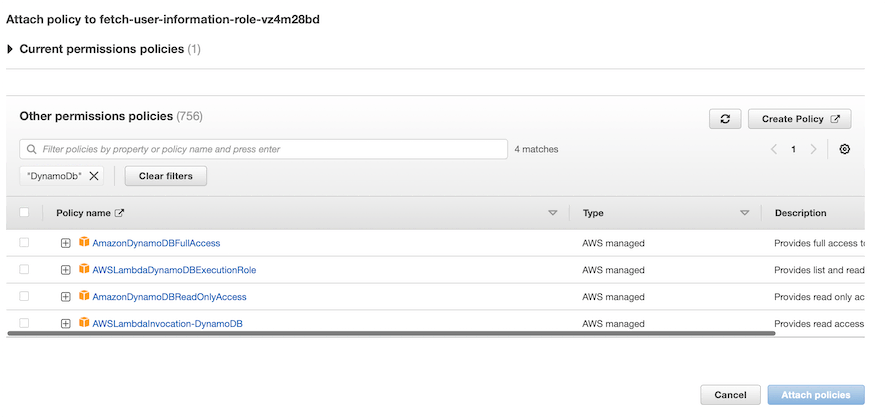
Afterward, you can add the required policies and click "Attach Policies." It may take a few seconds for the policies to attach to the Lambda role.
Then, you can execute DynamoDB operations from the service without any permission error.
Selecting "Create Inline Policies"
However, if you select "Create Inline Policies," you are free to create a custom inline policy with fine-tuned resource access. For example, you can provide a service to only perform a "query" operation and not a "create" operation.
The below figure shows the Create Policy wizard.
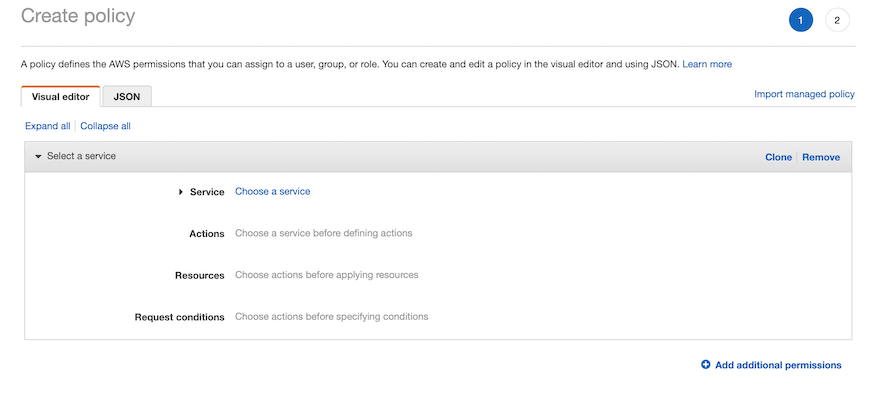
Figure - Creating inline policies.
Using the above wizard, you can provide the "DynamoDB" service and select the actions that the service can execute on the permitted resources (table ARNs).
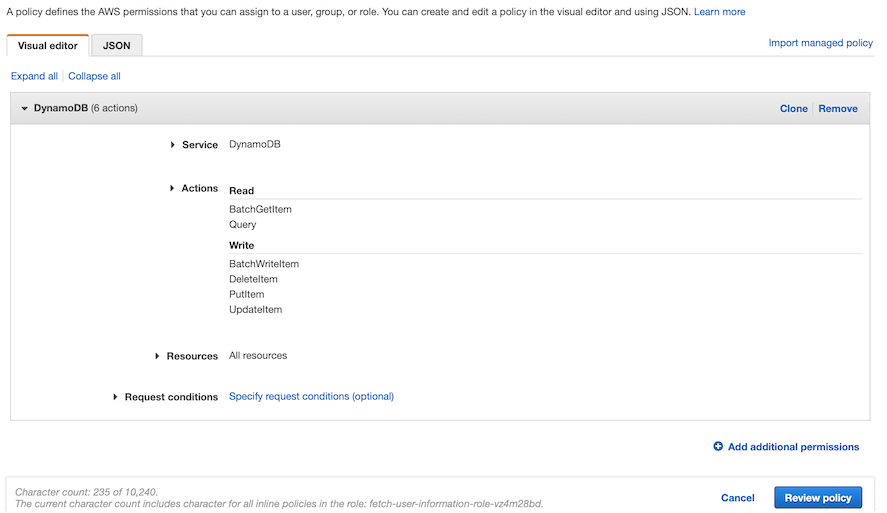
Figure - Defining the custom policy for DynamoDB access
After configuring the authorized actions on the defined resources, click "Review Policy" to review the inline policy.
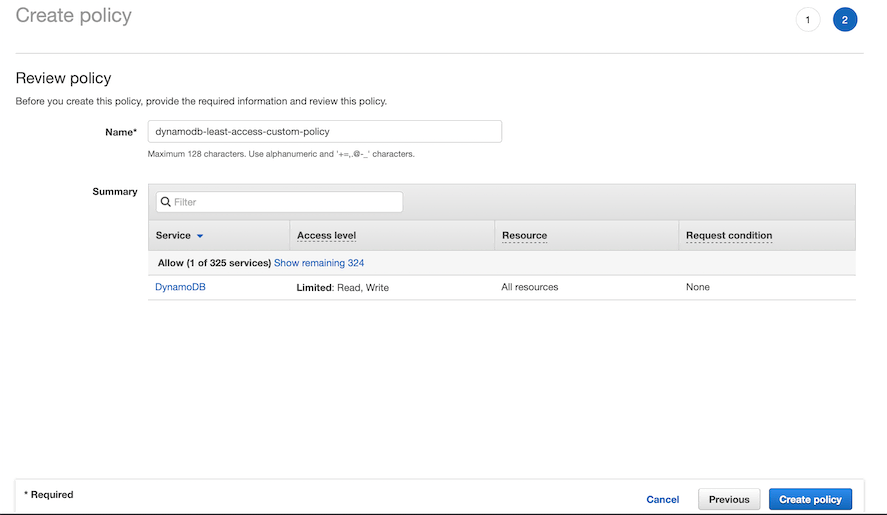
Figure - Reviewing the inline policy
After confirming the permissions, click "Create Policy" to create and bind the policy to the role. With this, developers can implement the principle of least privilege and fine-tune permissions.
Afterward, you can execute the operation in the service, and it will not throw a permissions error.
Other Common DynamoDB Errors (with Solutions)
- DynamoDB throttling error
- dynamodb problem function call failed
- DynamoDB No Regionendpoint Or Serviceurl Configured
- dynamodb is abstract cannot be instantiated
- dynamodb exclusivestartkey not working
- dynamodb query is not null
- dynamodb localhost not working
- dynamodb could not load credentials from any providers
- dynamodb consistent reads are not supported on global secondary indexes
- error retrieving dynamodb table item serializationexception
- dynamodb scan missing values
- dynamodb unknown error
- DynamoDB parameter validation failed
- DynamoDB error 400
- dynamodb throughput error