DynamoDB Encryption - Everything You Need To Know

Written by Lahiru Hewawasam
Published on March 16th, 2022
Time to 10x your DynamoDB productivity with Dynobase [learn more]
Introduction
Storing sensitive data while adhering to strict security and regulatory compliances puts an additional burden on teams. One component that all regulations mandate is encryption. For example, an unauthorized entity would not have the ability to read and understand the data being saved within the tables even if they have access to the table. DynamoDB also implements these capabilities into its functions to take the burden off its users. DynamoDB encryption features are available in all standard AWS Regions.
How Does DynamoDB Encryption Work?
The encryption available within DynamoDB helps configure an added layer of security so that the data transmitted will not be visible to any third parties. It supports both client-side encryption and encryption at rest.
DynamoDB implements its encryption in:
- Data at rest
- Data in transit
The data will be encrypted and signed before being sent to AWS DynamoDB. While being stored, the data will go through an encryption process, thus providing end-to-end protection against man-in-the-middle attacks and unauthorized changes to the data.
Data At Rest Encryption
Data at rest, also known as server-side encryption, refers to encrypting the data stored within the DynamoDB tables. DynamoDB uses industry-accepted standard AES-256 algorithms, ensuring that only authorized personnel and services can access sensitive data, while AWS CloudTrail audits this access to the encryption keys. It will encrypt its primary key, local and global secondary indexes, columns, streams, global tables, backups, and DynamoDB Accelerator (DAX) clusters.
It is important to note that an AWS managed KMS key will encrypt the data at rest when creating a new DAX cluster with the encryption at rest option enabled.
You can also use the AWS CloudFormation function to create the table while configuring the type of key used for the table's encryption.
Encryption at rest integrates with AWS KMS (Key Management Service) to manage the encryption key used to encrypt your tables.
When creating a new table, you can choose one of the following AWS KMS keys to encrypt your table:
- AWS owned key – Default encryption type. DynamoDB owns this key, and there will be no additional charge.
- AWS managed KMS key – Your account stores this key, and AWS KMS will handle the key management; therefore, AWS KMS charges will apply.
- Customer managed key – You entirely manage this key; your account is responsible for creating and managing this key. It allows complete control over the KMS key. AWS KMS charges will apply.
DynamoDB decrypts the data transparently when you access an encrypted table. You can switch between the AWS owned key, AWS managed KMS key, and customer managed key at any given time.
You do not have to change any applications or code to use or manage the encrypted tables; instead, you can use the AWS Management Console, AWS Command Line Interface (AWS CLI), or the Amazon DynamoDB API. In addition, you can refer to the DynamoDB guide on managing encryption keys for more information.
DynamoDB also assures that it will continue to deliver the same single-digit millisecond latency even when the tables are encrypted, and all DynamoDB queries will continue to work seamlessly on your encrypted data.
By default, DynamoDB enables encryption at rest, and you will not have an option to enable or disable this feature. All tables are encrypted using an AWS owned key in the DynamoDB service account. However, you can select the option to encrypt some or all of your tables using a customer managed key, or the AWS managed KMS key for DynamoDB in your account.
Data In Transit Encryption
Data in transit refers to encrypting your sensitive data while being transferred to and from DynamoDB. It ensures that your plaintext data isn't available to any third party, including AWS itself. Encrypting data in transit is achieved using the DynamoDB encryption client, a software library. The encryption client is provided free of charge under the Apache 2.0 license.
The DynamoDB encryption client will let you encrypt and sign the items within your table when added to the table. It also allows you to verify and decrypt the data when retrieved. This mechanism is also known as client-side encryption. It supports most features made available by Amazon DynamoDB, including global tables; however, it is important to note that older versions of global tables may require you to change some configurations before you start using the encryption client.
The DynamoDB encryption client allows for secure implementations that can encrypt the attribute values within each item in a table using a unique encryption key. In addition, it will enable you to protect against unauthorized changes by signing the items; unauthorized changes include deleting or adding attributes or swapping encrypted values.
You can use encryption keys from multiple sources, including custom cryptography services such as AWS CloudHSM or AWS Key Management Service (AWS KMS), when using the DynamoDB Client.
The DynamoDB encryption client libraries are currently available in Java and Python. The different programming languages used for its implementation are interoperable, meaning that you can encrypt data with the Java client and decrypt it with the Python client.
However, the DynamoDB Encryption Client is incompatible with the AWS Encryption SDK or the Amazon S3 Encryption Client. Therefore, you cannot encrypt with one client-side library and decrypt with another.
DynamoDB Backup Encryption
DynamoDB backups are encrypted, and the table restored from a backup also has encryption enabled. You can use the AWS owned key, AWS managed KMS key, or customer managed key to encrypt your backup data.
DynamoDB Global Tables Encryption
By default, DynamoDB enables encryption of all your data stored within tables with an AWS KMS (Key Management Service) key. However, when using a customer managed customer master key in KMS to encrypt your data within DynamoDB global tables, each regional replica of your global table requires an in-region customer managed key. Therefore, you can use customer managed CMKs (Customer Master Key) in all AWS regions with the global tables feature present.
AWS KMS Keys
By default, DynamoDB will use an AWS owned key; this is a key created and managed by AWS in a DynamoDB service account. But you can encrypt your DynamoDB tables using a customer managed key or an AWS managed KMS key in your AWS account. In addition, you can use a different KMS key for each table. The same KMS key you select is also used to encrypt its local and global secondary indexes, streams, and backups.
Changing the KMS keys is seamless and does not require downtime or degraded service. You can change these KMS keys for a table in the DynamoDB console or by using the UpdateTable operation.
When to use a customer managed key
When you want to create and manage the KMS key, include setting the key IAM policies and grants to control its access. You want to enable and disable the KMS key, enable and disable automatic key rotation, and delete the KMS key when it is no longer in use.
You want to use the customer managed key with imported key material, or a customer managed key in a custom key store that you own and manage.
You want to audit the encryption and decryption of your DynamoDB table by examining the DynamoDB API calls to AWS KMS in AWS CloudTrail logs.
When to use an AWS managed KMS key
You want to view the KMS key and its policy, but you do not want to change the key policy.
You want to audit the encryption and decryption of your DynamoDB table by examining the DynamoDB API calls to AWS KMS in AWS CloudTrail logs.
Conclusion
In this article, I have discussed DynamoDB encryption and how you can use it to improve security posture while adhering to compliances and security regulations.
I hope you have found this helpful. Thank you for reading!
Frequently Asked Questions
Is DynamoDB encrypted by default?
Yes, by default, DynamoDB enables encryption at rest by using an AWS owned key, and there is no option to enable or disable this feature.
Can we enable encryption on an existing DynamoDB table?
DynamoDB will encrypt all new tables that you would create by default using an AWS owned key. However, DynamoDB has already encrypted any older tables present within the service by using an AWS owned key.
Does AWS automatically encrypt DynamoDB data in transit?
No, the DynamoDB encryption client encrypts data in transit; this client is available in Java and Python.
How to check if DynamoDB is encrypted?
You can use AWS CloudShell to check if your tables are encrypted. For example, the following command will give you the description of the table, and within this output, locate the "SSEDescription" parameter:
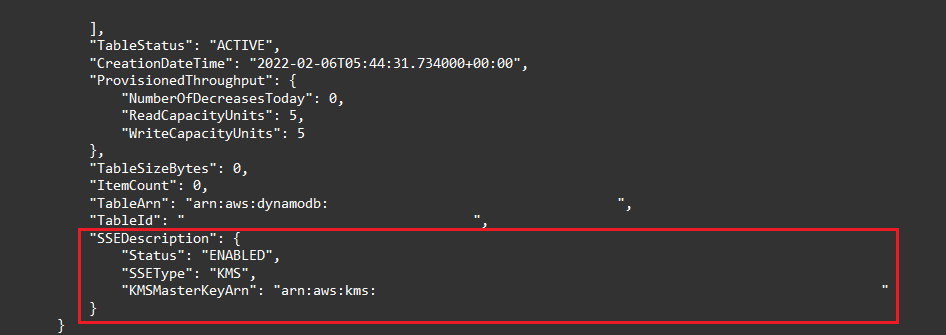
or use the following command to output only the necessary parameters: