DynamoDB Access Control - The Ultimate Guide

Written by Rafal Wilinski
Published on April 25th, 2020
Time to 10x your DynamoDB productivity with Dynobase [learn more]
Accessing DynamoDB is different from traditional databases. Most of us are probably accustomed to long-lived connections to SQL databases authenticated using a username and password combination. DynamoDB, however, uses a different approach. In this article, we'll cover the essentials of DynamoDB access control.
Access Control & DynamoDB Security Best Practices
Access to DynamoDB is secured using IAM (Identity and Access Management). This means you need a valid AWS Identity to authenticate your requests, and that identity must have sufficient permissions to create or access DynamoDB resources. Authentication in AWS can be achieved in several ways:
- Using the AWS account root from the AWS console or using a pair of access and secret keys. This method is highly discouraged due to the significant security risks associated with using root credentials.
- Using an IAM user from the AWS console or using a pair of access and secret keys.
- Using an IAM role which is attached to an IAM user or AWS resource, such as an AWS Lambda function or EC2 instance. IAM roles provide temporary security credentials and are a more secure option.
- Using AWS Vault, an open-source tool that issues temporary credentials from long-lived IAM identities stored securely on your machine.
- Using AWS SSO, a cloud service that allows you to grant your users access to AWS resources.
How to Give Lambda Access to DynamoDB
Using Console
First, open the Lambda function that should have access to DynamoDB and head to the "Permissions" tab. On that tab, click "View Role Document".
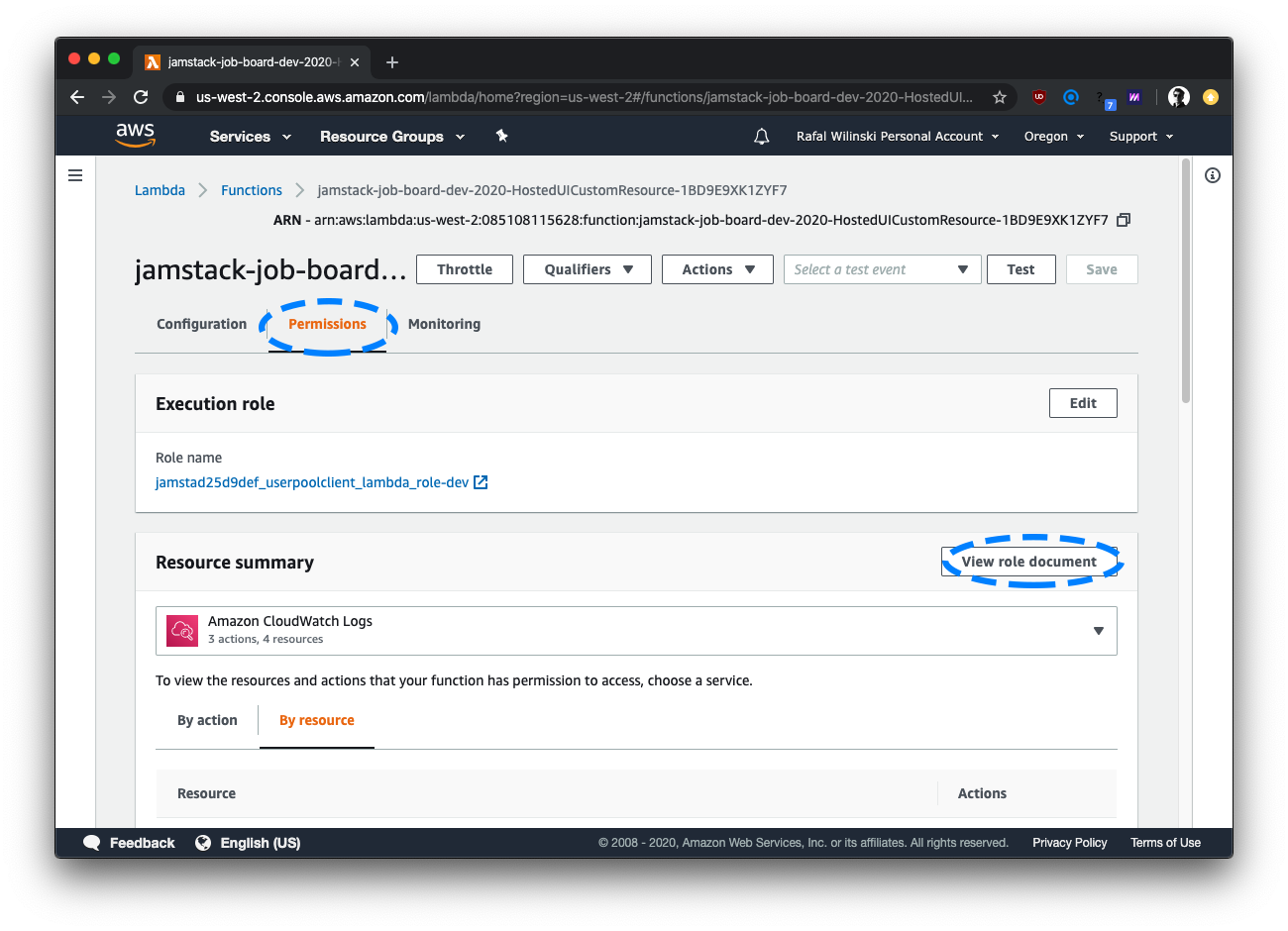
An editor should pop up. Add the following inline policy to the policies array:
This policy will give the Lambda function administrative permissions to <table-name>. Be cautious with the dynamodb:* action as it grants full access to the table. For more restrictive access, specify only the necessary actions.
Using Serverless Framework
Adding IAM permissions to your Lambda functions in Serverless is as easy as extending the provider.iamRoleStatements object like so:
How to Access DynamoDB From EC2
Accessing DynamoDB from an EC2 instance can be achieved in two ways:
- Using Access and Secret keys. The AWS SDK or CLI will use a pair of strings stored in the
~/.awsdirectory or using environment variables. This method is not recommended as it poses a security risk. - Using an IAM role. This is the preferred way where your instance gets an IAM role assigned and uses it to perform actions against AWS resources. More on that here.
AWS IAM & DynamoDB Read-Only Policy
If you want to give your teammates read-only access to the databases, you can use the following IAM Policy:
This policy will allow them to list all of the tables in the AWS account but read the data only from the <table-name> table.
Understanding DynamoDB Fine-Grained Control
Fine-Grained Access Control for DynamoDB allows you to restrict access to specific rows and columns in the table using IAM policies. It can be useful for:
- A multiplayer game table that stores high scores. You want to display users' scores and their nicknames but probably do not want to expose their emails. In a case like this, a "Vertical" IAM Condition lets you selectively hide specific attributes of all the DynamoDB items in a particular table by matching on attribute names.
- A metadata store. You probably won't want to expose all the records to every user, only the ones they own. In a case like this, a "Horizontal" IAM Condition lets you selectively show only specific records.
More on that on the official AWS blog.
Permissions Required by Dynobase for DynamoDB
Dynobase can be used with DynamoDB in two modes - read-only or read-write.
To use Dynobase in read-only mode, make sure to give your role/policy the following permissions:
If you want to be able to make data modifications through Dynobase, include the following IAM actions as well:
Best Practices for DynamoDB Security
To ensure the security of your DynamoDB tables, follow these best practices:
- Use IAM roles instead of access keys: Assign IAM roles to your AWS resources (e.g., EC2 instances, Lambda functions) to avoid the security risks associated with long-lived access keys.
- Enable encryption at rest: Use AWS KMS to encrypt your DynamoDB tables to protect sensitive data.
- Enable point-in-time recovery: This feature allows you to restore your table to any point in time within the last 35 days, providing an additional layer of data protection.
- Monitor and audit access: Use AWS CloudTrail to log and monitor all access to your DynamoDB tables. This helps in identifying and responding to unauthorized access attempts.
- Implement least privilege access: Grant only the permissions necessary for users and applications to perform their tasks. Regularly review and update IAM policies to ensure they adhere to the principle of least privilege.
Additional Considerations for DynamoDB Security
When designing your DynamoDB security strategy, consider implementing VPC endpoints for DynamoDB. This allows you to keep traffic between your VPC and DynamoDB within the AWS network, enhancing security by avoiding exposure to the public internet. Additionally, consider using AWS WAF (Web Application Firewall) to protect your applications from common web exploits that could affect availability, compromise security, or consume excessive resources. Regularly review and update your security policies and practices to adapt to new threats and ensure compliance with industry standards and regulations.
By following these best practices and additional considerations, you can enhance the security and reliability of your DynamoDB tables, ensuring that your data remains protected and accessible only to authorized users.